Security log sheet example in title
This Microsoft Excel spreadsheet program that creates professional and complete business/travel expense reports. It's ideal for small or...
Commercial 93.3 KB Download
Takes advantage of the power and familiarity of Microsoft Excel to automate your customer invoice creation. The workbook comes with sample data to...
Commercial 4.91 MB Download
This Microsoft Excel spreadsheet creates a professional time-billing invoice for customers. Type in the week-ending date, and the rest of the days of...
Commercial 2.03 MB Download
Text Log Monitor (TLM) provides Systems Administrators the ability to monitor and filter local or remote text log files as well as alert all in...
Commercial 2.12 MB Download
my Math Quiz Sheets is a program designed to created printable math homework sheets. An extensive range of options allow you to fully customize the...
Commercial 366 KB Download
Security log sheet example in description
VisualSniffer is a powerful packet capture tool and protocol analyzer (ip sniffer or packet sniffer) for Windows system. VisualSniffer can be used by...
Freeware 3.07 MB Download
The Securepoint Intrusion Detection System (SIDS) allows to analyse your network for intrusion detections. SIDS protects your network from illegal...
Freeware 1.31 MB Download
LogQuest VF is a Log analysis tool for all types of logs that searches information in any log. By analyzing security data from mixed devices...
Commercial 53.12 MB Download

Active Directory change auditing is an important procedure for limiting unauthorized changes and errors to AD configuration. One single change can...
Freeware 4.01 MB Download
With BriefAudit, every user can easily find the answer. Just right click on the file FOO and select Properties [using Windows 2000 Explorer] or...
Commercial 2.48 MB Download
As every IT manager knows, security is a trade-off between usability and the level of protection required. For example, to prevent users making...
Commercial 8.87 MB Download
When you are working on your computer performing the day to day activity like surfing the Internet, paying your bills online and logging into the...
Commercial 933.32 KB Download
eSTOP! was developed as a security product with the intent to view and (e)mergency STOP problem TCP connections. It displays in real-time any TCP...
Commercial 758 KB Download
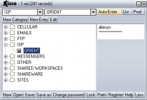
Xizzo (pronounced ziz-zo) is a thumb drive friendly password manager utility that helps users securely store their log-in information and enter it...
Commercial 765.19 KB Download
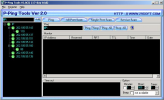
If you are charge in administration of network , this software will be a quite useful tool for your detecting network work. It has many...
Commercial 1.22 MB Download
More related searches
- security patrol log sheet template
- security camera log sheet
- security activity log sheet
- example security patrol log sheet
- security officer log sheet
- security officer log sheet template
- security control log sheet template
- security guard daily activity log sheet
- security daily log sheet on word
- log sheet security patrol