Disable write protect tool in title
Document XML messages to send to the server as well as messages expected back, and you can run automated unit tests at any time. While there is no...
Freeware 21 KB Download
Tired of Boring Toolbars? Liven up the Word workplace with this attractive set of colored toolbar icons. The complete collection comes with 3 full...
Commercial 301 KB Download
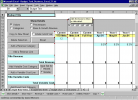
The Budget Tool Business Excel provides an effective means to generate a budget for up to five years. Full flexibility allows you to add Revenue...
Commercial 586.95 KB Download
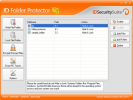
ID Folder Protector is a very easy to use program, designed to help you maintain the privacy of your personal data. It locks, hides, encrypts and...
Commercial 1.42 MB Download
Disable write protect tool in description
If you are administrator and you want to identify unauthorized use of USB storage device activities in your local area network then try our USB data...
Commercial 2.84 MB Download
USB device data protection software is powerful and professional real time USB activities monitoring tool that avoids network from unofficial use of...
Commercial 2.84 MB Download
Are you worried about how to disable USB storage device and how can limit access of storage media on windows network? Then no need to worry about...
Commercial 2.84 MB Download

Tons of kid-friendly tools, all in a fully integrated kid-safe environment. Includes easy-to-use tools for children to Write, Draw, Paint...
Commercial 6.97 MB Download
So far users have had to use a combination of various attack types (brute-force, dictionary attack, brute-force with mask, Xiew attack) to recover...
Commercial 0 B Download
USB port controller offers confidence that how to protect systems without resorting to drastic measures such as a complete ban on USB drives and...
Commercial 2.84 MB Download
USB monitoring software helps you to identify unauthorized use of USB storage device activities in local area network. USB data theft monitoring...
Commercial 2.84 MB Download
CHM To Exe lets you convert Microsoft HTML Help files (.chm) into secure and stand-alone applications (EXE files). With CHM To Exe, open CHM files...
Freeware 1.67 MB Download
Block Application can able to lock programs to access by other with tool help. Websites protection is other part to blocks domain to enable or open....
Commercial 4.8 MB Download
IP Anonymizer is a privacy protection tool that hides your IP address preventing your surfing habits and your internet activity over the Internet...
Commercial 2.45 MB Download