Mom blow dad and son in title
Accounts and Budget 2000 gives you all necessary tools to manage your budget and your bank accounts. Manage your expenses, income and transfers...
Commercial 6.24 MB Download
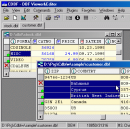
CDBF is a small yet powerful application designed for viewing and editing DBF database files. This tool features full control over the DBF files...
Commercial 3.47 MB Download
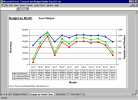
The Forecast and Budget Builder Excel is a streamlined tool for developing a 3 year business forecast and a 12 month budget. It requires minimal...
Commercial 792.57 KB Download
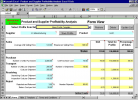
Determine your profit by product and supplier. Product and Supplier Profitability allows you to identify the true costs associated with your...
Commercial 444 KB Download
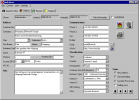
hed.dress is intended for professional use. Addresses can be found quickly, even while speaking on the phone. By writing reports you can track...
Commercial 10.52 MB Download
Mom blow dad and son in description
An arcade style underwater escapade in full color 3D animation! Bubble popping fun for everyone! Meet your friend, Bubbly. Bubbly must navigate his...
Commercial 9.66 MB Download
Dangerous Activity 3D is a new head-scratching puzzle. If you are a fan of Microsoft's Minesweeper, then its idea and rules should be familiar...
Commercial 6.79 MB Download

In this game you need to help the penguins cross the river. The penguins come in pairs of father and son. When the father is not around, the son will...
Freeware 259.21 KB Download
A combined 32 bit Windows 95/98/2000/ME client/server which incorporates strong blowfish encryption and the FTP protocol (RFC 959 implementation) to...
528 KB Download
SecureCRT for Windows, Mac, and Linux provides rock-solid terminal emulation, secure remote access, file transfer, and data tunneling for IT...
Commercial 14.7 MB Download
SecureCRT for Windows, Mac, and Linux provides rock-solid terminal emulation, secure remote access, file transfer, and data tunneling for IT...
Commercial 8.6 MB Download

This is a secure X-server for Windows with SSH encryption. Run UNIX applications on your PC, transforming it into a fully functional X-terminal....
Commercial 20.22 MB Download
With BestCrypt you allocate a portion (container) of free space on your drive where you keep all your sensitive data in encrypted form, creating a...
Commercial 3.91 MB Download
With CryptoMagic you may create & use virtual encrypted disks for protection from LAN & Internet intruders. You may work with these virtual...
Commercial 2.31 MB Download
Fully blown point and click e-commerce turnkey solution for merchants the world over. Used to conduct e-business in over 30 countries it can create...
Commercial 7.81 MB Download