Men of war key generator in title
A sophisticated but inexpensive POS system suitable for small, standalone businesses. Features include Multi-payment Cash Sales, Invoicing...
Commercial 4.01 MB Download
Demolish all the bricks while avoiding the flying Birds Eggs. Fifty graphical Levels with 10 different Bonuses to help you to succeed against those...
Commercial 4.77 MB Download
The War of All-Time is a game where you try and fight the evil OF, (Overpower Force), and restore Time to its original state. Fight against Spitfires...
1.63 MB Download
The logical game, a variety of the game Filler, based on capturing by the contenders adjacent color fields. Wins the one who will capture a majority...
Commercial 367 KB Download
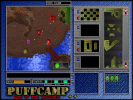
PuffCamp is a combination action and puzzle game! Explore an intricately-crafted island as you try to assemble complex keycards, rescue POW's...
Commercial 9.52 MB Download
Men of war key generator in description

If you want to be always in time, have your clock at hand and know the exact hours and minutes any moment you wish while using your personal...
Commercial 14.91 MB Download

If you run a bar, a restaurant, a shop, a casino, a dance club or even a radio station, music becomes one of your key daily priorities. Music is what...
Commercial 13.73 MB Download
PPC-PROTECT - the system of software protection for Windows CE (PocketPC) applications with ARM core, designed for quick implementation of...
Commercial 655 KB Download
A handy tool that generates random hexidecimal wireless network keys for your Wi-Fi (802.11a/b/g) networks with WEP (128-bit/40-bit) or WAP...
Freeware 81 KB Download
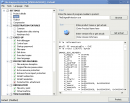
A professional system for licensing and protecting executable files for Windows. The Enigma Protector is an essential tool for every developer of...
Commercial 13.69 MB Download
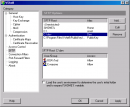
VShell Secure Shell server is a secure alternative to Telnet and FTP on Windows and UNIX platforms. VShell provides the strong encryption, robust...
Commercial 3.62 MB Download
Itcan be used to run trial periods of software forpredefined periods and then expire or continue runningwith various parts of the application it...
Commercial 1.52 MB Download
This is the best protection that you can ever place on the software that you develop at the best price ever. We have many happy customers in a verity...
Commercial 3.64 MB Download
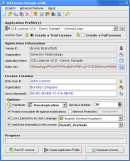
ICE License Protection is providing a high barrier against illegal copy using the power of Elliptic Curvesl Asymmetric Encryption to protect your...
Commercial 4.94 MB Download
"try-before-you-bWith ICE License it's easy to turn your application in "try-before-you-b versions with little effort, offering everything to...
Commercial 4.94 MB Download