John persons pass in title
The PDF Password Remover COM can be used to decrypt protected Adobe Acrobat PDF files, which have "owner" password set, preventing the file...
Freeware 199 KB Download
ID Executable Password is a program meant to protect by the use of a password all Windows executables. It modifies the content of the existing .EXE...
Commercial 1.07 MB Download
Protected Passwords Base means storing your passwords, logins, credit card numbers, and any other confidential data in a strongly encrypted password...
Commercial 808 KB Download
A full featured easy to use Password Manager and Generator with unlimited Category support, Copy / Paste, Go to Website, Auto Fill Website, Password...
Commercial 5.26 MB Download

Forgot your word password? Pwdspy Word password recovery tool is the best word password recovery tool to recover word password due to forgotten or...
Commercial 4.9 MB Download
John persons pass in description
If you have busy email traffic and you need timesaving templates, this program is for you. Create the Templates as easily as you create a new email...
Commercial 6.77 MB Download
A database requested by our company managers. Some of the requests it had to fulfill were: Intuitive user interface. Fast data entry, without mouse...
Commercial 1.36 MB Download
...They live not far from your house... Just over the fence from the last cottage on your street there's a dump. Not a romantic place, huh? But...
Freeware 3.7 MB Download
GENERAL Flexcrypt is a small software application that enables encryption and decryption of your emails. The reason for encrypting is to ensure the...
Freeware 1.21 MB Download
...They live not far from your house... Just over the fence from the last cottage on your street there's a dump. Not a romantic place, huh? But...
Freeware 4.6 MB Download
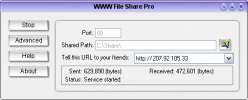
WWW File Share Pro can help you share files on the internet or on the local area network. You may use it to share files between your PC and other...
Commercial 2.68 MB Download
...They live not far from your house... Just over the fence from the last cottage on your street there's a dump. Not a romantic place, huh? But...
Freeware 2.53 MB Download
Less involvement of IT staff Password reset requests form a substantial part of all helpdesk calls. Such requests often show a peak on Monday...
Commercial 6.03 MB Download
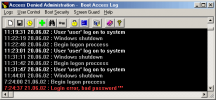
Security program requests username and password or simple password upon boot-up and locks desktop by one mouse click. It can't be bypassed on...
Commercial 523 KB Download
Keystroke monitoring software proves to be the best surveillance tool for the persons who think that others are using their system when they are away...
Commercial 72 KB Download