Bat algorithm example in title
The Bat! is a powerful, highly configurable, yet easy to use, email client for the casual user or the power user, the home or the office. Unlimited...
Commercial 16.3 MB Download
We are proud to present you our unique image comparison algorithm implemented as standalone dll file. It has only one exported function with two...
Commercial 3.67 MB Download

Learning HTML and web design is easy if you have some reference point to work with. That's why we built the "Learn HTML By Example"...
Freeware 8.76 KB Download
Learn how to make custom print preview. Customize Rave report and make your own Custom Rave report. This report example has all the features you...
Commercial 661 KB Download
The statistical trainable classification algorithm has unique characteristics. It analyzes your private correspondence, singles out distinguishing...
Commercial 2.7 MB Download
Bat algorithm example in description
Advanced Maillist Verify (AMV) is a program that verifies the validity of e-mail addresses in databases, address books and mailing lists. Now...
Commercial 3.46 MB Download
A fast, highly optimized implementation of popular checksum algorithms: CRC32, CRC16, CRC16C (CRC-CCITT). The library allows to calculate checksums...
Commercial 269.47 KB Download
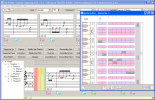
The Palette program is a tool for the creation of 'theoretically correct' melodies. The program is based on composition theory and the...
Commercial 1.97 MB Download
(*) Spam Trapper is a multilevel spam filter for Microsoft Outlook version 2000 and later. It is a plug-in component with clear convenient interface....
Commercial 493 KB Download

This e-mail encryption software uses 8192-bit RSA public key encryption and a secure 384-bit cipher, incorporating the AES candidate Twofish...
Freeware 2.55 MB Download
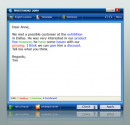
WhiteSmoke Enrichment software performs, for the first time in language software history, sentence processing as opposed to word-by-word processing....
Commercial 1000 KB Download
Passwords, logins, credit cards, private plans, ideas and thoughts; organize and securely store all of your private information in a strongly...
Freeware 1.09 MB Download
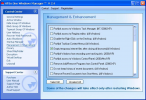
This is the tool Microsoft should have included with Windows. Instead of installing 15-20 deferent softwares, you can just install All In One...
Commercial 0 B Download
Isecure-key encrypt your USB disk, sticks or Pendrive with 256 bit AES encryption using the Truecrypt encryption software. It provide an easy front...
Commercial 5 MB Download
CryptoStorage is a reliable and easy-to-use system for encrypting private data on your Pocket PC and controlling access to it. The work of...
Commercial 191 KB Download