Law enforcement access templates 2010 in title
Nucleus Kernel Access is a advance easy to use access file repair software for corrupt [.mdb] files. Software uses QFSCI technology to repair corrupt...
Commercial 845 KB Download
Splitter is an excellent example of a utility that does a single task with pizzazz. This Microsoft Access 2002 add-in (there are versions for Access...
Commercial 1.74 MB Download
If you ever wanted to create an own CD-label, CD-box-inlet and CD-box-liner FOR FREE, here is the solution! You just need Word for Windows 95 and...
13 KB Download

The award-winning Teaching Templates suite is a varied and timesaving set of eight authoring tools that help you create interactive, web-based...
Commercial 5.73 MB Download
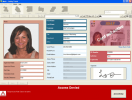
Lobby Track Access Control Software is a new secure tracking, access control, and visitor management software system. This innovative new technology...
Commercial 54.04 MB Download
Law enforcement access templates 2010 in description
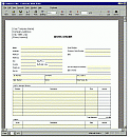
FormDocs for Windows Electronic Forms software includes everything you need to design and fill in any type of form for small business, big business...
Commercial 6.84 MB Download
Personality testing is now simple and affordable with Home Personality Test for Windows and Macintosh. A simple yet very powerful software, Home...
Commercial 1.36 MB Download
ESP+ Monitoring is an transparent easy-to-use monitoring and surveillance tool for personal PCs. ESP+ captures all users activity on the PC -...
Freeware 3.16 MB Download
NeoTrace Pro delivers a powerful tool for checking information on Internet site. You can trace any computer on the internet simply by entering an...
Commercial 1.39 MB Download
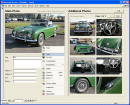
Add Images to Access Easily and Efficiently with DBPix: the Access Image Control. Avoid ALL the Access Imaging Gotchas! * Fast easy development * No...
Commercial 2.79 MB Download
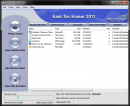
Protect your data and privacy and remove all evidence of your computer and online activity with East-Tec Eraser 2002. Eraser goes beyond U.S....
Commercial 2.22 MB Download
Protect your data and privacy and remove all evidence of your computer and online activity with East-Tec Eraser 2003. Eraser goes beyond U.S....
Commercial 2.22 MB Download
When a laptop is stolen it is not just the physical loss of a machine but also the valuable and sensitive information that it stores. Unfortunately...
Commercial 3.24 MB Download
Unique ability to invisibly monitor and record all keyboard activity placing it in the context of the active window make it ideally suited for the...
Commercial 6.94 MB Download

What is Cryptocx v5? Cryptocx is an encryption component designed for use in any modern development environment. Cryptocx encrypts and decrypts data...
Commercial 4.42 MB Download
More related searches
- access templates 2010 torrents
- ms access templates 2010 trucking
- ms access templates 2010 horse racing
- microsoft access templates 2010 medical
- access templates 2010 soccer
- access templates 2010 doctor
- access templates 2010 for medical
- access templates 2007 law enforcement
- ms access templates for law enforcement
- ms access and excel for law enforcement