Effective md5 hash decrypters in title
Developing Critical Thinking Skills for Effective Reading is reading comprehension software that motivates students to improve their reading skills...
Commercial 7.47 MB Download

Forensic examiners often need to quickly obtain the hash values for potential evidence files for reports or to verify their results. Pinpoint Hash...
Commercial 4.2 MB Download
By Softcomplete Development. HashTrie is a new high efficient data structure for fast searching. It combines in herself properties of the hash-tables...
Freeware 100.63 KB Download
What are you talking about? Ever find yourself in meetings that have no purpose? Ever find yourself in meetings where there's no agenda, no...
Commercial 2.93 MB Download
Simple logic game. You do steps serially with the computer. For the least number of steps you should grasp more blocks. After you will choose...
Commercial 1.28 MB Download
Effective md5 hash decrypters in description
MegaChart is an ActiveX (COM) component that allows to dynamically create professional looking charts of all common types (2d & 3d bars, pies...
Commercial 588 KB Download
Once we had a necessity to daily download certain files from ftp server. Our colleagues uploaded them to ftp, where files might have been updated...
Commercial 4.33 MB Download

CryptoTools is a multi-language suite of encryption components and libraries. CryptoTools provides DES and Triple DES (3DES) encryption, as well as...
Commercial 1.09 MB Download
AcuteFinder is a handy shareware utility that finds duplicate files on your computer. You can then delete the extra copies or move them to an archive...
Commercial 3.51 MB Download

IBillIt was the first, and is still the best, library certified by Authorize.net for their Automated Recurring Billing (ARB) service. IBillIt is...
Commercial 2.23 MB Download
MSCCrypto is COM component for Active Server Pages and stand-alone applications. It includes collection of the best encryption and hashing...
Commercial 225.35 KB Download
This tool can generate a TSIG key value (base64) for you very easily. The key value complies with RFC2845. Secret Key Transaction Authentication...
Freeware 143.5 KB Download
SecureBridge is a non-visual component library for Delphi, C++ Builder, Lazarus (and Free Pascal). It can protect any TCP network traffic using SSH...
Commercial 6.47 MB Download
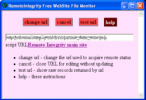
Protect your website from unauthorized changes (hacking). Protects against defacement (visible changes) and malware (invisible changes) via date...
Freeware 56.5 KB Download
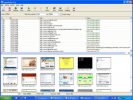
Snapshotter Pro is a Windows program that allows you to take screenshots and thumbnails of web pages or whole websites and convert html or text files...
Commercial 9.18 MB Download