Decrypt tool of sha algorithm in title
Document XML messages to send to the server as well as messages expected back, and you can run automated unit tests at any time. While there is no...
Freeware 21 KB Download
Tired of Boring Toolbars? Liven up the Word workplace with this attractive set of colored toolbar icons. The complete collection comes with 3 full...
Commercial 301 KB Download
A sophisticated but inexpensive POS system suitable for small, standalone businesses. Features include Multi-payment Cash Sales, Invoicing...
Commercial 4.01 MB Download
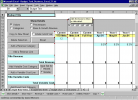
The Budget Tool Business Excel provides an effective means to generate a budget for up to five years. Full flexibility allows you to add Revenue...
Commercial 586.95 KB Download
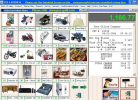
Easy to setup, and very easy to learn POS system with powerful features. A perfect solution to improve efficiency and profitability of your business...
Commercial 6.79 MB Download
Decrypt tool of sha algorithm in description
96Crypt features several worldwide trusted block ciphers algorithms such as: 3DES, Blowfish, MARS, RijnDael-AES, SERPENT or Twofish. All our block...
Commercial 1.56 MB Download
Adware Spyware Be Gone offers a Free Download. Try it for FREE. Scan your system for adware, spyware, keyloggers, and malware products. Adware...
Commercial 5.35 MB Download
MusicWonk is a MIDI program that produces MIDI music based on algorithmic rules that you interactively create by connecting modules (graphical...
Commercial 5.91 MB Download
GIPALS32 is a linear programming library that incorporates the power of linear programming solver and simplicity of integration to any software tools...
Commercial 680.12 KB Download
The Palette program is a tool for the creation of 'theoretically correct' melodies. The program is based on composition theory and the...
Commercial 1.97 MB Download

Lightweight component that provides strong encryption for your applications. It provides supports for most common crypto algorithms, such as AES...
Commercial 4.27 MB Download
Passwords, logins, credit cards, private plans, ideas and thoughts; organize and securely store all of your private information in a strongly...
Freeware 1.09 MB Download
Typically you encrypt files because you don't want others to see them, but sometimes you want to send someone an encrypted file. Most if not all...
Commercial 5.86 MB Download
Typically you encrypt files because you don't want others to see them, but sometimes you want to send someone an encrypted file. Most if not all...
Commercial 5.86 MB Download
Encryption Workshop includes file and folder encryption and decryption tool. Currently nine strong symmetrical block ciphers are implemented:...
Commercial 2.71 MB Download