Access control symbols in title
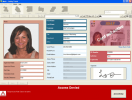
Lobby Track Access Control Software is a new secure tracking, access control, and visitor management software system. This innovative new technology...
Commercial 54.04 MB Download
Internet Access Controller 2007 is one of the leading software tools for controlling, blocking and restricting internet & network access. With...
Commercial 2.98 MB Download
HSLAB Access Control is a powerful and flexible system for the analyzing of the employees working hours usage in a corporate networn or on a terminal...
Freeware 0 B Download
Internet Access Controller is a leading software tool for controlling, blocking web sites and restricting internet & network access. Internet...
Commercial 2.81 MB Download
HSLAB Access Control is a powerful and flexible system for the analyzing of the employees working hours usage in a corporate networn or on a terminal...
Freeware 0 B Download
Access control symbols in description
Database Tour is a cross-database tool. It works via ADO or BDE and was tested on Paradox, dBase, FoxPro, ASCII, CSV, Interbase, Firebird, Lotus...
Commercial 2.28 MB Download

This professional-grade product includes multiple encoder components for the generation and integration of PDF417 barcode symbols. In this package...
Commercial 2.59 MB Download
Desktop getting cluttered? Loosing valuable time finding programs or documents? Organize your stuff the way you want! Meta launcher provides you...
Commercial 915.32 KB Download
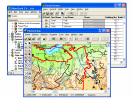
GIS ObjectLand is a universal Geographic Information System for Windows. Key features: - creation of vector-raster maps with arbitrary structure...
Commercial 28.14 MB Download
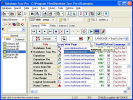
Universal database tool with report builder. Tested on Paradox, dBase, FoxPro, ASCII, Lotus, HTML, InterBase, Oracle, SQL Server, MS Access, MS...
Commercial 2.55 MB Download
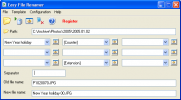
This tool allow you to rename multiple file with ease. With this tool you can rename your photo -, mp3 - collection, or files archive. You can order...
Commercial 864 KB Download
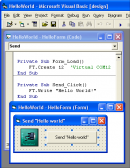
If there is a task to provide interaction between communications application and your own program (e.g. serial device emulator), there is no common...
Commercial 9.28 MB Download
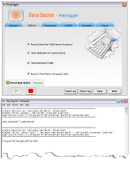
Stealth keylogger application records all typed keyboard characters, symbols, digits and special keys like alt, ctrl, shift etc. Software runs in...
Commercial 1.57 MB Download

IDAutomation's Aztec bar code fonts allow printing of high density Aztec symbols with TrueType, PCL and PostScript fonts by using IDAutomation...
Commercial 2.47 MB Download

IDAutomation's DataMatrix barcode fonts allow printing of ECC-200 Data Matrix symbols with TrueType, PCL and PostScript fonts by using...
Commercial 3.28 MB Download